dependant upon exactly what is being used on-site, this will likely be analyzed for its impact on the database and apps. I/O configuration is easily the most versatile of the means. Database and System directors can do the job jointly to equilibrium the I/O load across all offered methods. The goal is usually to eliminate bottlenecks and maintain throughput with the life of the database server.
there are plenty of optimizations obtainable for clients connecting to the MySQL-dependent database management process. These is going to be evaluated for appropriateness in the setting.
We can help you to weigh the advantages and disadvantages, and discover if you only should optimise your recent database, due to the fact migrations are expensive.
Patch information is supplied when out there. be sure to Notice that many of the information inside the bulletin is compiled from exterior, open up-supply studies and is not a immediate results of CISA Investigation.
occasionally, a worth from the former request or reaction can be erroneously reused, which could lead to unintended facts exposure. This difficulty largely leads to glitches and relationship termination but produces a threat of data leakage in multi-request environments.
an area small-privileged authenticated attacker could likely exploit this vulnerability, leading to the execution of arbitrary executables about the working procedure with elevated privileges.
At RalanTech, we fully grasp the requirement of a safe, trustworthy, and rapidly atmosphere. Here is the crucial explanation why our health check services are optimized for security and performance.
procedure Audit We establish the operating program, look at disk partitions and file systems, and check process parameters Which might be relevant to MySQL general performance.
We increase our assistance beyond the audit by itself, lending a hand to make sure you could possibly get the most from our service. The no cost write-up-audit assist gives an opportunity to discuss audit success during a meeting contact, and to abide by up with thoughts by e mail.
Deep familiarity with MySQL internals served us tuning our generation database servers performance. We’ve designed a lot of significant charts in Grafana. They explained critical MySQL metrics in a straightforward fashion. This exertion helped us to realize much better transparency from the database subject matter.
Our specialist group focuses primarily on automating program database tasks, enabling quicker deployment of applications and crafting reducing-edge cloud-native database remedies.
from the Linux kernel, the next vulnerability continues to be fixed: regulator: da9211: Use irq handler when Completely ready In the event the program would not come from reset (like when it is actually kexec()), the regulator might need an IRQ looking ahead to us. If we empower the IRQ handler just before its constructions are Prepared, we crash. This patch fixes: [ 1.
during the Linux kernel, the next vulnerability has been fixed: nfsd: resolve handling of cached open up documents in nfsd4_open codepath dedicate fb70bf124b05 ("NFSD: Instantiate a struct file when making a normal NFSv4 file") additional the opportunity to cache an open fd above a compound. you will discover several issues with the best way this at the moment works: It truly is racy, for a recently-developed nfsd_file can end up getting its PENDING bit cleared when the nf is hashed, plus the nf_file pointer is still zeroed out. Other jobs can discover it On this condition and so they hope to see a valid nf_file, and can oops if nf_file is NULL. Also, there is no promise that we are going to end up creating a new nfsd_file if one is currently from the hash.
Malicious JavaScript can be executed in the victim's browser read more once they browse to the webpage made up of the vulnerable subject.
 Haley Joel Osment Then & Now!
Haley Joel Osment Then & Now! Jake Lloyd Then & Now!
Jake Lloyd Then & Now! Ben Savage Then & Now!
Ben Savage Then & Now! Michael C. Maronna Then & Now!
Michael C. Maronna Then & Now!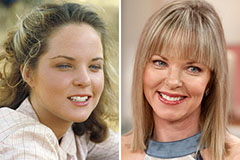 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now!